Server-side Template Injection (SSTI)
What is SSTI?
Web applications frequently use template systems to embed dynamic content in web pages and emails.
For instance, ASP framework (Razor), PHP framework (Twig, Symfony, Smarty, Laravel, Slim, Plates), Python frameworks (django, mako, jinja2), Java frameworks (Groovy, Freemarker, Jinjava, Pebble, Thymeleaf, Velocity, Spring, patTemplate, Expression Language EL), Javascript frameworks (Handlebars, Codepen, Lessjs, Lodash), Ruby framework (ERB, Slim).
Server-side Template Injection vulnerabilities (SSTI) occur when user input is trusted when embedding a template, which is an unsafe implementation and might lead to remote code execution on the server.
OWASP
OWASP Web Security Testing Guide 4.2 > 7. Data Validation Testing > 7.18. Testing for Server-side Template Injection
| ID | Link to Hackinglife | Link to OWASP | Description |
|---|---|---|---|
| 7.18 | WSTG-INPV-18 | Testing for Server-side Template Injection | - Detect template injection vulnerability points. - Identify the templating engine. - Build the exploit. |
Resources for these notes
Payloads
Snipped of vulnerable source code:
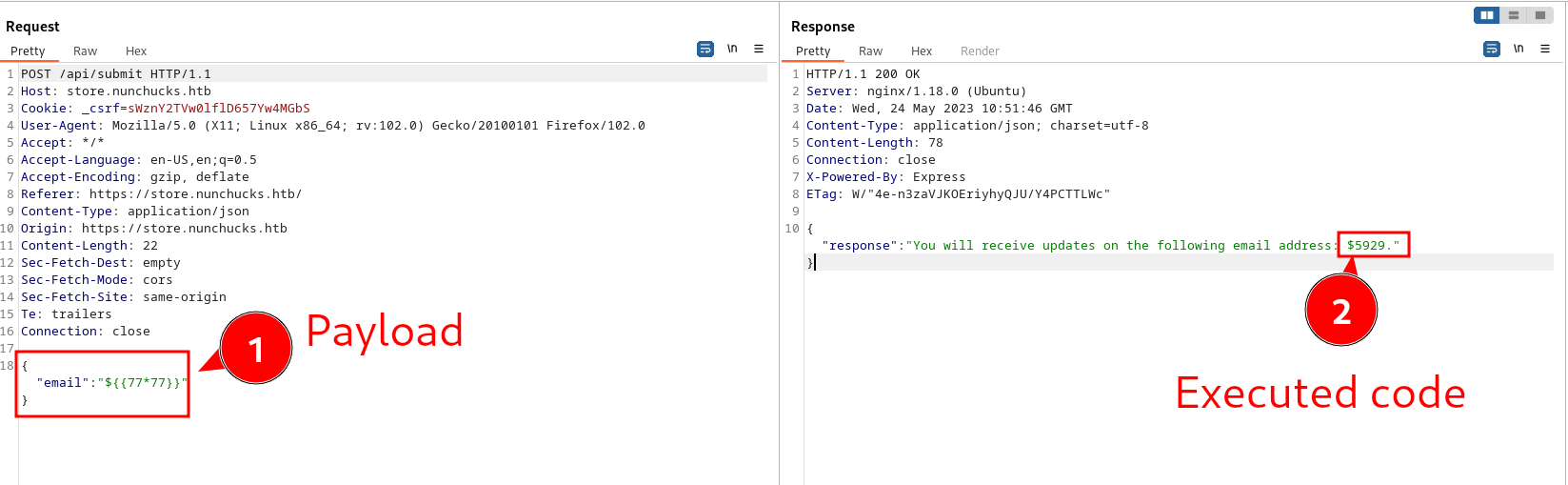
What we have here is essentially server-side code execution inside a sandbox. Depending on the template engine used, it may be possible execute arbitrary code directly or even to escape the sandbox and execute it. Following the example, in this POST request the expected email value has been replaced by a payload and it gets executed:
Exploitation
1. Detect injection points
Template languages use syntax chosen explicitly not to clash with characters used in normal HTML, so it's easy for a manual blackbox security assessment to miss template injection entirely. To detect it, we need to invoke the template engine by embedding a statement.
Here’s a simple example of using Twig in a PHP application. This would be the exampletemplate.twig:
And the PHP rendering the Twig template:
Now, coming back to our web app, we could curl the following:
With SSTI the response would be:
Trick:There are a huge number of template languages but many of them share basic syntax characteristics. We can take advantage of this by sending generic, template-agnostic payloads using basic operations to detect multiple template engines with a single HTTP request. This polyglot payload will trigger an error in presence of a SSTI vulnerability:
2. Identify the template engine
After detecting template injection, the next step is to identify the template engine in use.
Green and red arrows represent 'success' and 'failure' responses respectively. In some cases, a single payload can have multiple distinct success responses - for example, the probe {{7*'7'}} would result in 49 in Twig, 7777777 in Jinja2, and neither if no template language is in use.
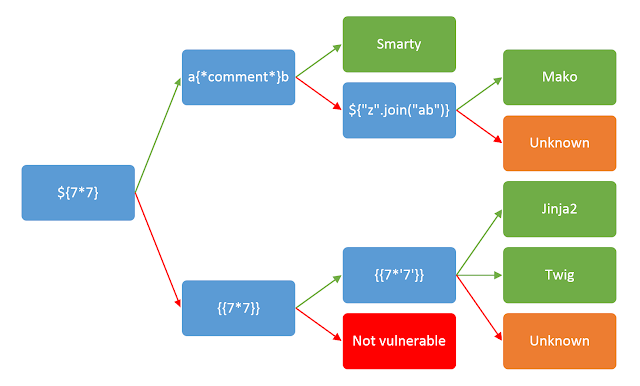
Payloads for different Template engines
3. Exploitation
Once you discover a server-side template injection vulnerability, and identify the template engine being used, successful exploitation typically involves the following process.
-
Read
- Template syntax
- Security documentation
- Documented exploits
-
Explore the environment:
Many template engines expose a "self" or "environment" object of some kind, which acts like a namespace containing all objects, methods, and attributes that are supported by the template engine. If such an object exists, you can potentially use it to generate a list of objects that are in scope.
It is important to note that websites will contain both built-in objects provided by the template and custom, site-specific objects that have been supplied by the web developer. You should pay particular attention to these non-standard objects
- Create a custom attack
1. Java frameworks
Many template engines expose a "self" or "environment" object. In Java-based templating languages, you can sometimes list all variables in the environment using the following injection:
This can form the basis for creating a shortlist of potentially interesting objects and methods to investigate further. Additionally, for Burp Suite Professional users, the Intruder provides a built-in wordlist for brute-forcing variable names.
1.1. FreeMarker
Basic payloads:
RCE in FreeMarker:
1.2. Velocity
RCE in Velocity:
2. PHP frameworks
2.1. Smarty
RCE in Smarty
3. Python frameworks
3.1. Mako
RCE in Mako
3.2. Tornado
Basic payloads:
RCE in Tornado:
Useful tips to create SSTI exploit for Tornado:
- Anything coming between {{ and }} are evaluated and send back to the output.
{{ 2*2 }} -> 4
- {% import module %} - Allows you to import python modules.
{% import subprocess %}
4. Ruby frameworks
4.1. ERB
Basic injection:
Retrieve /etc/passwd
List files and directories
Code execution
Tools
- Tplmap
- Backslash Powered Scanner Burp Suite extension
- Template expression test strings/payloads list
Related lab
HackTheBox: Nunchunks: Express server with a nunjucks template engine.
Last update: 2024-05-01 Created: May 24, 2023 17:04:33