Evasion and Combining techniques
General index of the course
- Setting up the environment
- Api Reconnaissance.
- Endpoint Analysis.
- Scanning APIS.
- API Authorization Attacks.
- Exploiting API Authorization.
- Testing for Improper Assets Management.
- Mass Assignment.
- Server side Request Forgery.
- Injection Attacks.
- Evasion and Combining techniques.
- Setting up the labs + Writeups
Resources
Here some basic techniques for evading or bypassing common API security controls.
What can trigger a WAF (Web Applicatin Firewall)?
- Too many requests for inexisting resources.
- To many requests in a short period of time.
- Common SQL or XSS payloads attackes in requests.
- Unusual behaviour (like a test for authorizathion vulnerabilities).
How to detect a WAF
What can a WAF do provided that RESTful APIs are stateless? They can use attribution to identify an atacker and for that they use: IP address, origin headers, authorization tokens and metadata (patterns of requests, rate of requests and the combination of the headers included in the requests).
When it comes to Hacking APIs the best approach is first use the API as it was intended. Second, review the API responses for evidence of a WAF (in headers):
1. Headers such as X-CDN means that the API is leveraging a Content Delivery Network (CDN), which often provides WAFs as a service.
2. Use Burp Suite's Proxy and Repeater to watch if your requests are being sent to a proxy (302 sending you to a CDN).
3. Use some tools:
Also w3af, WAFW00f, and this recollection of handy tools: waf-bypass.com.
Great article found when searchin for these tools: hacken.io.
Techniques for evasion
1. Burners accounts
So there is a WAF. Before attacking, create several extra accounts (or tokens you can dispose). Watch out! When creating these accounts, make sure you use information not associated to your other accounts:
1 2 3 | |
2. Bypassing controls with string terminators
Null bytes and other combinations of symbols are often interpreted as string terminators. When not filtered out they could terminate the API security control filters.
Here an example of a NULL byte included in a XSS combined with a SQL injection attack.
3. Bypassing controls with case switching
Case switching the payload may provoke the WAF not detecting the attack.
4. Bypassing controls by encoding payloads
If you are using Burp Suite, the module Decoder is perfect for quickly encoding or decoding a payload.
Trick: double encoding your payload.
Tools
1. BurpSuite Intruder
Also, once you know which encoding technique is the efective one to bypass the WAF, use BurpSuite Intruder (section Payload processing under the Intruder Payload option) for configuring you attack. Intruder has some more worthy options:
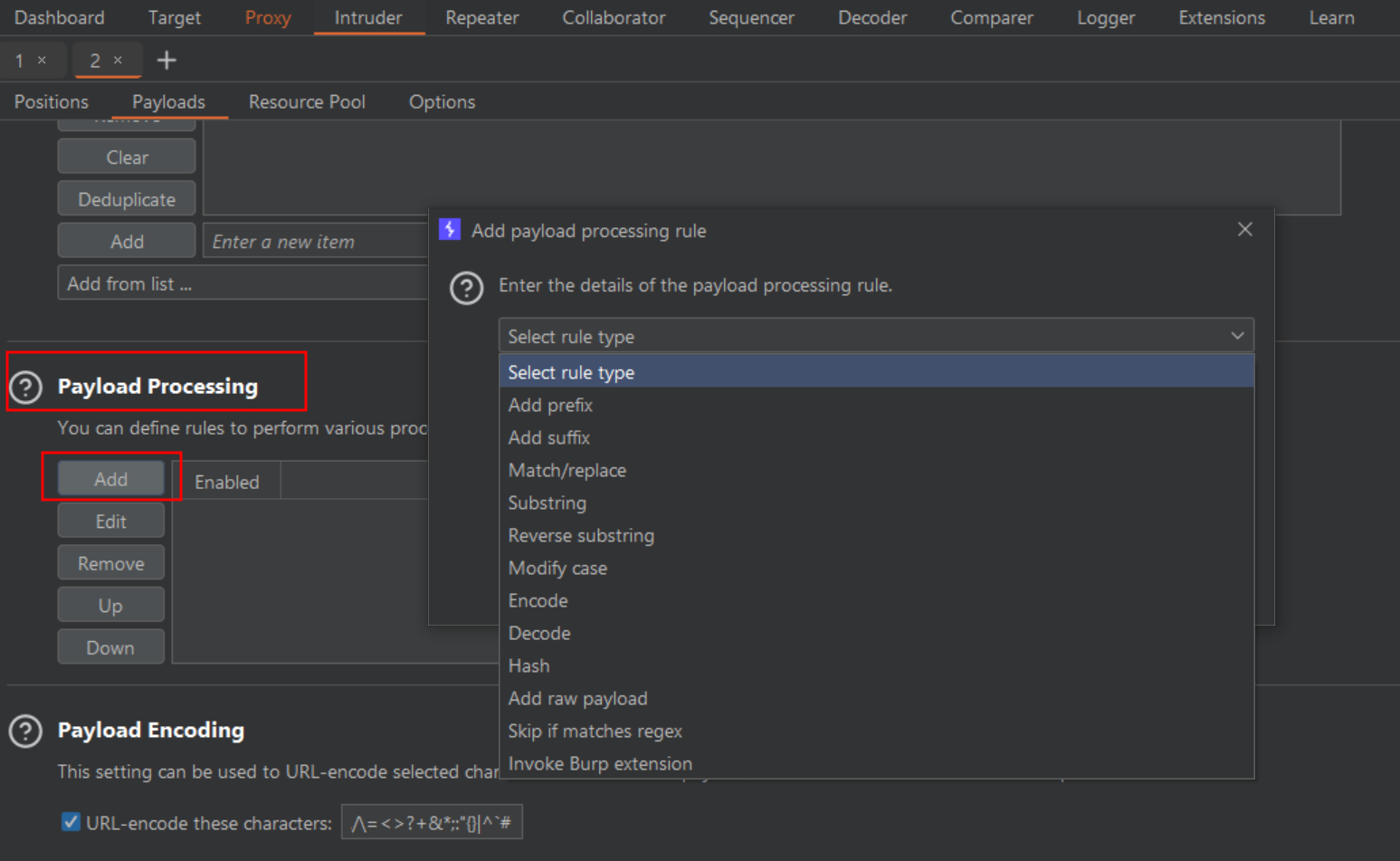
2. wfuzz
Testing rate limits
Rate limits. What for?
- To avoid incurring into adittional costs associated with computing resources.
- To avoid falling victim to a DoS attack.
- To monetize.
How to know if rate limit is in place
- Consult API documentation.
- Check APIs header (x-rate-limit, x-rate-limit-remaining, retry- after).
- See response code 429.
Techniques
1. Throttle your scanning
In wfuzz:
In BurpSuite:
2. Bypassing paths
When altering slightly the URL path, this could cause the API provider to handle the request diferently, potentially bypassing the rate limit.
- Adding null bytes.
- Altering the string ramdonly with various upper and lower case letter.
- Adding meaningless parameters.
3. Modifying Origin headers
When the API provider use headers to enforce rate limiting, you could manipulate them:
- X-Forwarded-For
- X-Forwarded-Host
- X-Host
- X-Originating-IP
- X-Remote-IP
- X-Client-IP
- X-Remote-Addr
4. Modifying User-agent header
You can use this dictionary: Seclist.
Rotating IP addresses with BurpSuite
Add the extension IP Rotate.
Requirements to install IP Rotate and have it working:
- Install the tool Boto3.
- Install the Jython standalone file from https://www.jython.org/download.html.
- You will need an AWS account in which you can create an IAM user. There is a small cost associated with using the AWS API gateway. After downloading the IAM Services page, click Add Users and create an user account with programmatic access selected. On the "Set Permissions page", select "Attach Existing Policies Directly". NExt filter policies by searching for "API". Select the "AmazonAPIGatewayAdministrator" and "AmazonAPIGatewayInvokeFullAccess" permissions. Preceed to the review page.. No tags needed. Skip ahead and create the users. Now, download CSV file containing your user's access key.
- Install IP Rotate
- Open the IP Rotate Module and copy and paste access key from the user added in IAM service.