Information gathering phase - Thick client Applications
General index of the course
Tools
CFF Explorer Detect It Easy Process Monitor Strings
What we will be doing
1. Understand the functionality of the application.
2. Architecture diagram from the client.
3. Network communications in the app.
4. Files that are being accessed by the client.
5. Interesting files within the application directory.
Tools: CFF explorer, wireshark, and sysInternalsSuite.
IP addresses that the app is communicating with
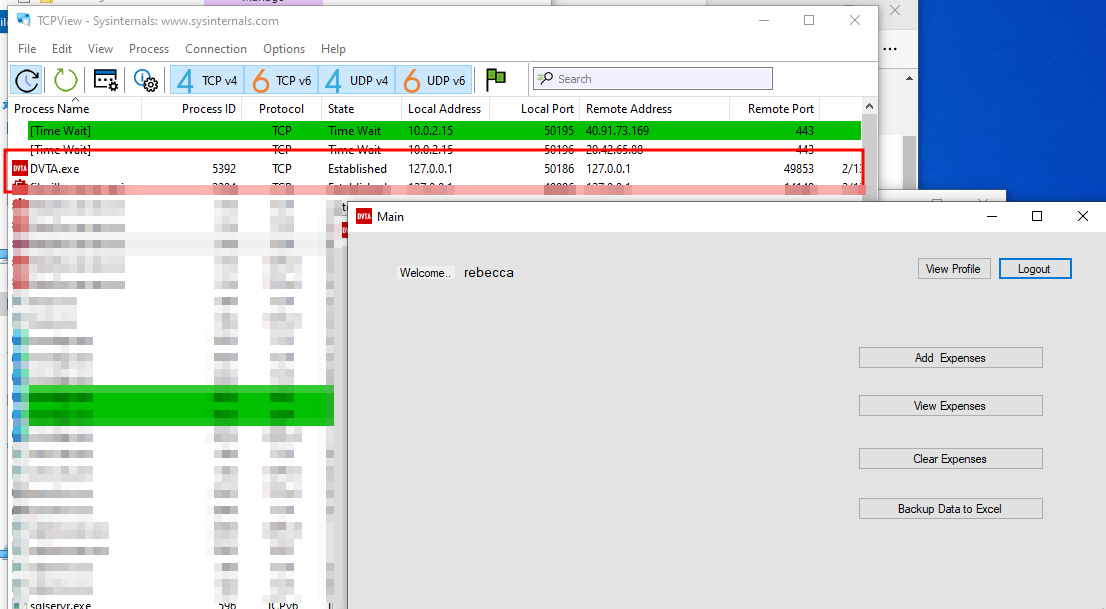
TCP View
To see which IP addresses is the app communicating with, we can use TCP View from sysInternalsSuite.
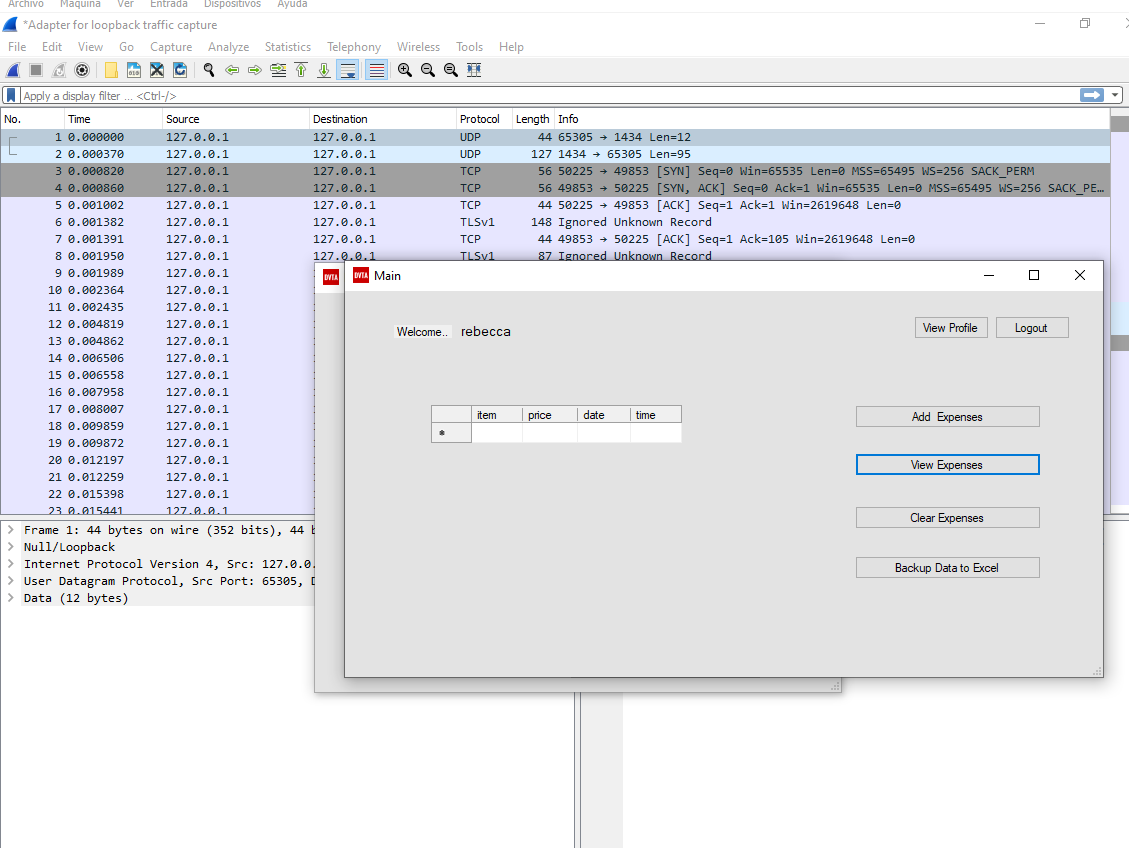
Wireshark
We can also use wireshark
Language in which the app is built in
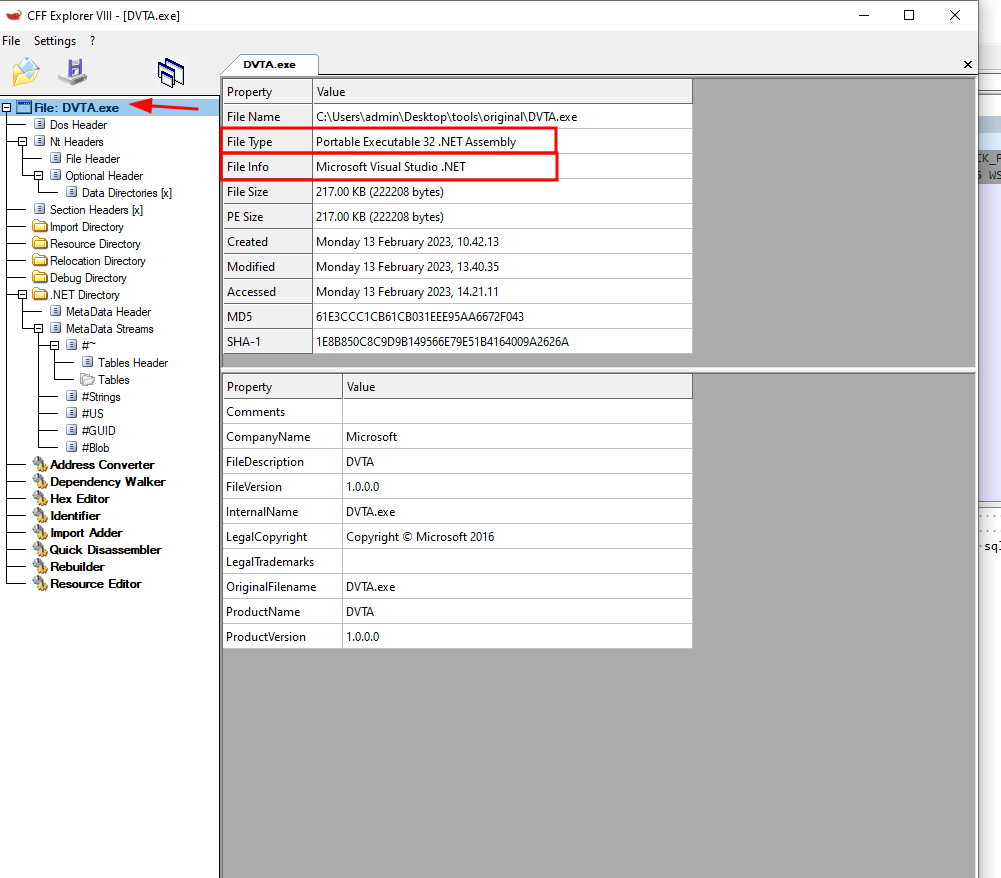
CFF Explorer
To see which language is the app build in, and which tool was used, we can use CFF explorer. Open the app with CFF Explorer.
Changes in the FileSystem
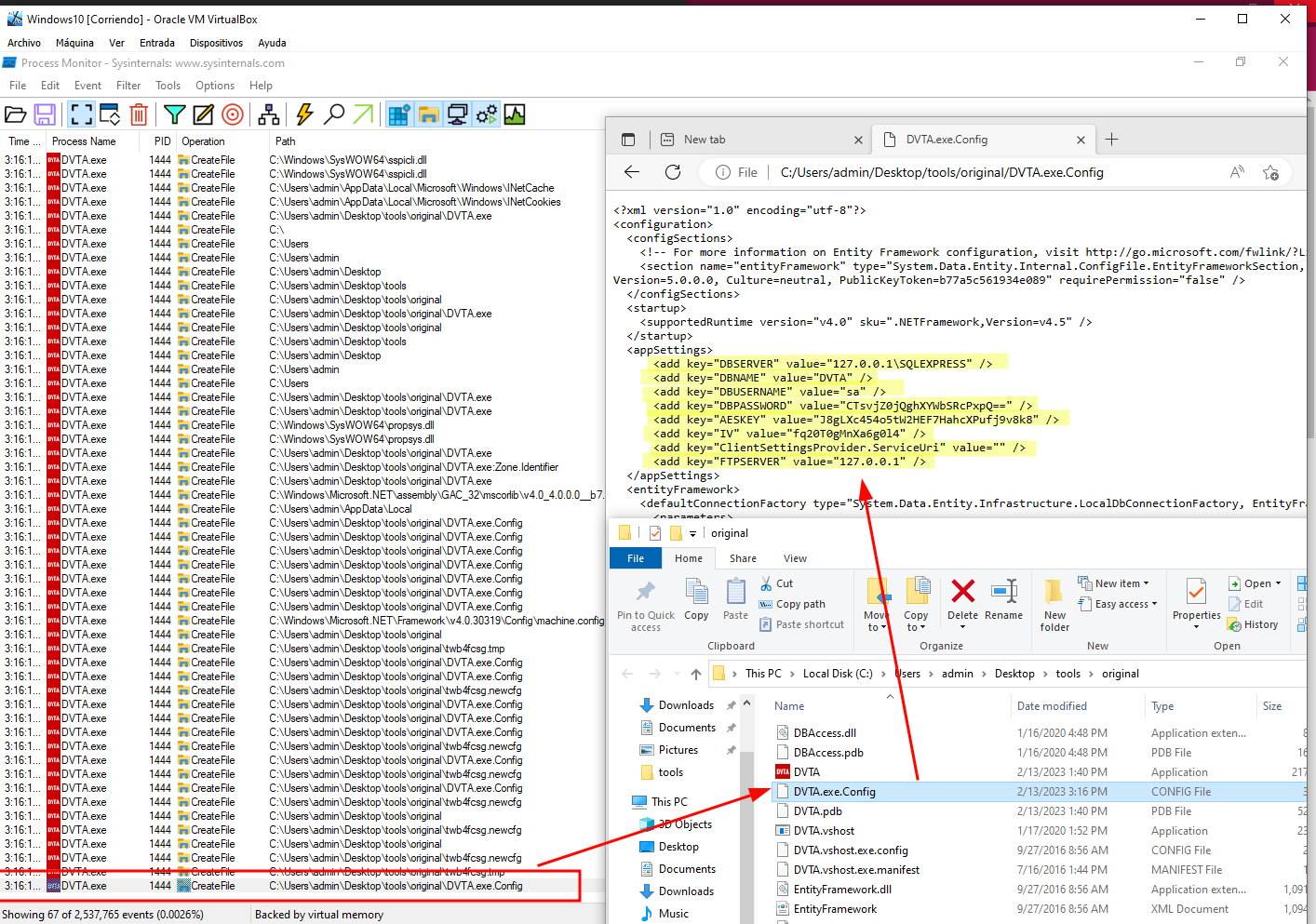
ProcesMonitor
Use ProcessMonitor tool from sysInternalsSuite to see changes in the file system.
For instance, you can analyze the access to interesting files in the application directory. Now we have this information:
Locate credentials and information in Registry entries
ProcessMonitor
Using ProccessMonitor from sysInternalsSuite to locate credentials and information stored in the key registers. And for that, after cleaning all the processes in ProcMon (ProcessMonitor app), you close the application and reopen it.
If the session is still there, it means that the session is saved somewhere. In this case the session is saved in the registry keys.
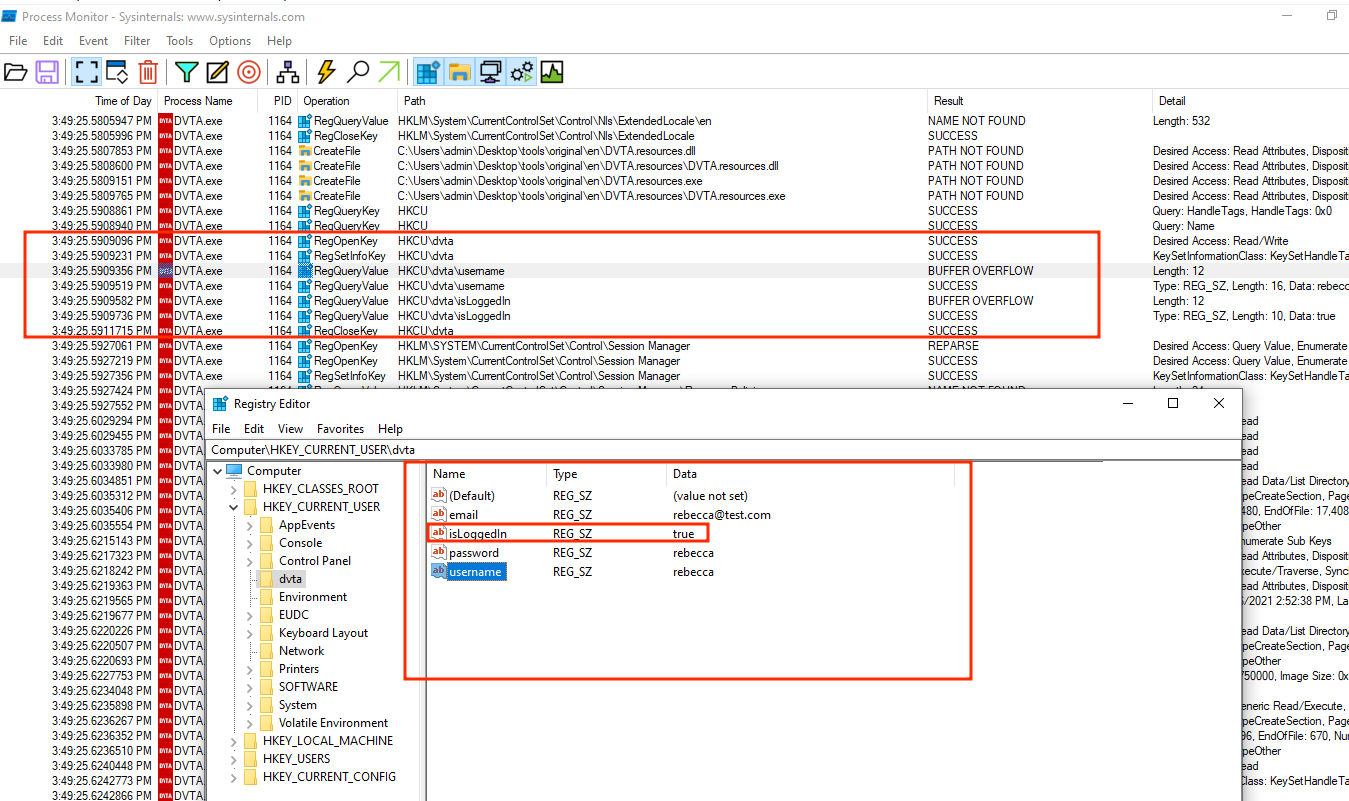
Interesting thing here is the Registry Key "isLoggedIn". We could try to modify the boolean value of that registry to bypass login.
Also, check these other tools and resources:
Enumerate libraries and resources employed in building the app
When pentesting a thick-client application, I came across this nice way to enumerate libraries, dependencies, sources... By using Sigcheck from sysInternalsSuite, you can view metadata from the images with executables. Additionally, you can save the results to a CSV for reporting purposes.
One cool flag is the recursive one ("-s"), which helps you avoid navigating through the folder structure.
Last update: 2025-02-09 Created: February 16, 2023 21:24:34