CSRF attack - Cross Site Request Forgery
OWASP
OWASP Web Security Testing Guide 4.2 > 6. Session Management Testing > 6.5. Testing for Cross Site Request Forgery
| ID | Link to Hackinglife | Link to OWASP | Description |
|---|---|---|---|
| 6.5 | WSTG-SESS-05 | Testing for Cross Site Request Forgery | - Determine whether it is possible to initiate requests on a user's behalf that are not initiated by the user. - Conduct URL analysis, Direct access to functions without any token. |
Cross Site Request Forgery (CSRF) is a type of web security vulnerability that occurs when an attacker tricks a user into performing actions on a web application without their knowledge or consent. A successful CSRF exploit can compromise end user data and operation when it targets a normal user. If the targeted end user is the administrator account, a CSRF attack can compromise the entire web application.
CSRF vulnerabilities may arise when applications rely solely on HTTP cookies to identify the user that has issued a particular request. Because browsers automatically add cookies to requests regardless of the request's origin, it may be possible for an attacker to create a malicious web site that forges a cross-domain request to the vulnerable application.
Three conditions that enable CSRF:
- A relevant action.
- Cookie-based session handling.
- No unpredictable request parameters.
How it works
CSRF attacks can have serious consequences:
- Unauthorized changes to a user's account settings.
- Fund transfers or actions on behalf of the user without their consent.
- Malicious actions like changing passwords, email addresses, or profile information.
How to test CSRF by using Burpsuite proof of concept
Burp has a quite awesome PoC so you can generate HTML (and javascript) code to replicate this attack.
-
Select a URL or HTTP request anywhere within Burp, and choose Generate CSRF PoC within Engagement tools in the context menu.
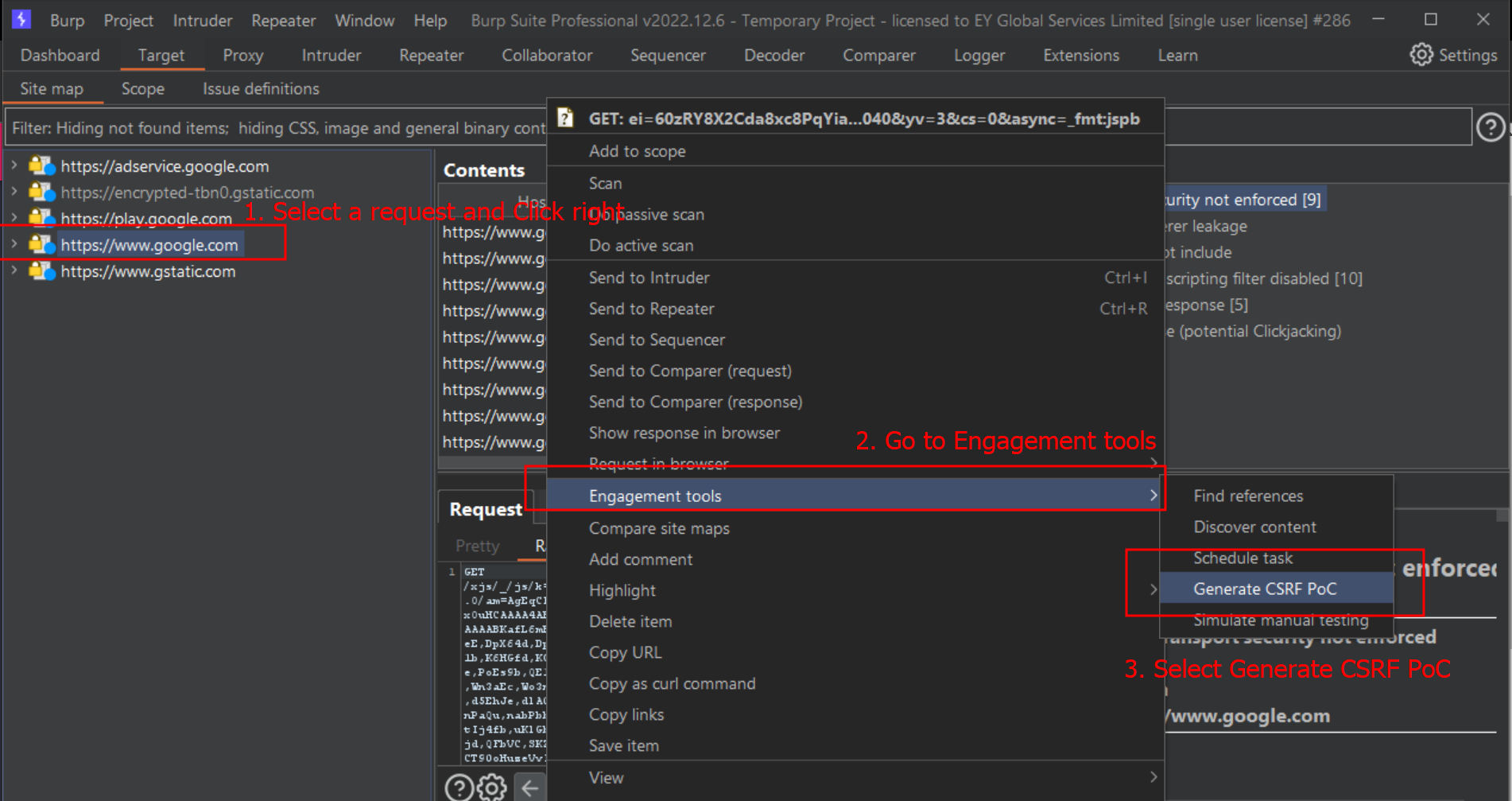
-
You have two buttons: one for editing the request manually (Regenerate button) the HTML based on the updated request; and tje ptjer to test the effectiveness of the generated PoC in Burp's browser (Test in browser button).
-
Open the crafted page from the same browser where the user has been logged in.
-
Observe the result, i.e. check if the web server executed the request.
Fetch API
Requirements:
- Authentication Method should be cookie based only
- No Authentication Token in Header
- Same-Origin Policy should not be enforced
Browser -> Network tab in development tools, right click on request and copy as fetch:
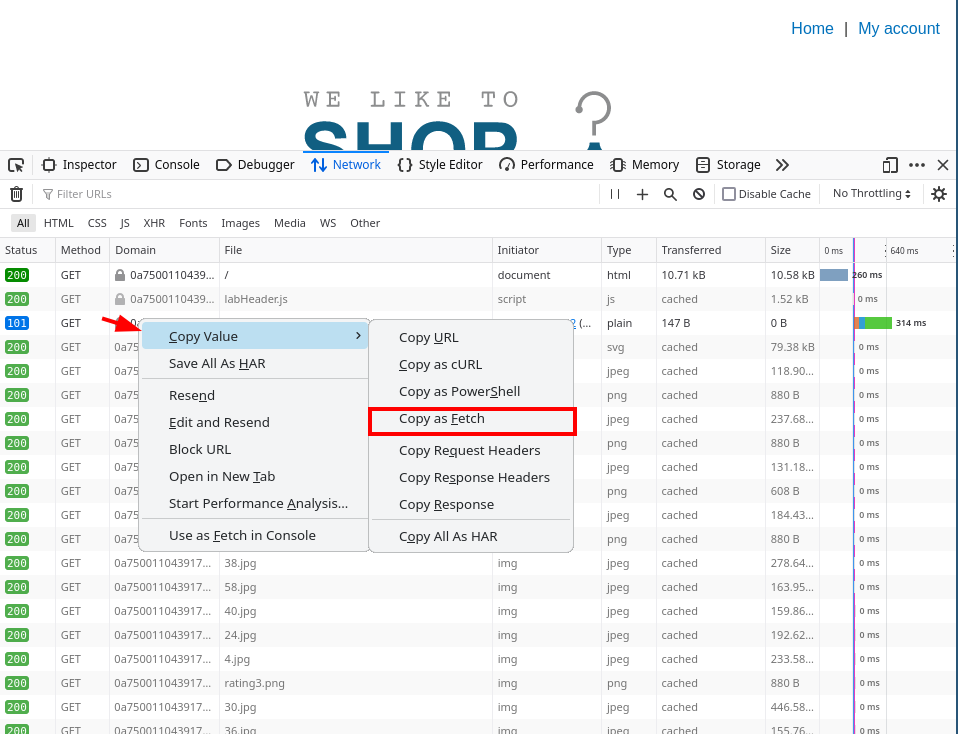
Json CSRF
Resources: https://systemweakness.com/ways-to-exploit-json-csrf-simple-explanation-5e77c403ede6
POC: source rootsploit.com
Mitigation
Cross-Site Request Forgery Prevention Cheat Sheet
Related labs
Resources
When it comes to web vulnerabilities, it is useful to have some links at hand:
- Owasp vuln description: https://owasp.org/www-community/attacks/csrf.
- Using Burp to Test for Cross-Site Request Forgery (CSRF): https://portswigger.net/support/using-burp-to-test-for-cross-site-request-forgery.
- PoC with Burp, official link: https://portswigger.net/burp/documentation/desktop/functions/generate-csrf-poc.
Tools and payloads
- See updated chart: Attacks and tools for web pentesting.