JWT tool
JWT attacks
Two tools: jwt.io and jwt_tools.
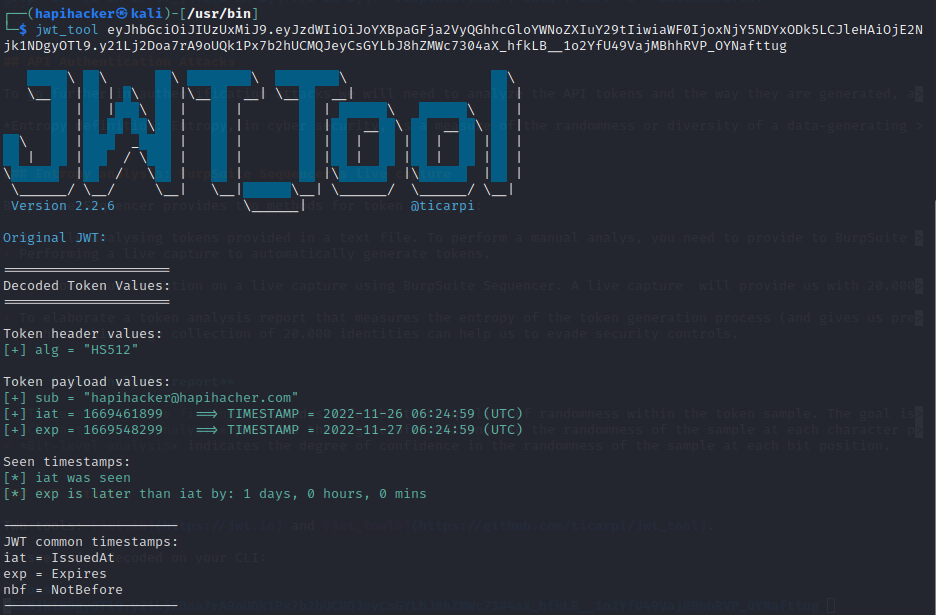
To see a jwt decoded on your CLI:
Result:
Also, to see the decoded jwt, knowing that is encoded in base64, we could echo each of its parts:
Results:
To run a JWT scan with jwt_tool, run:
Example:
Some more jwt_tool flags that may come in hand:
The none attack
A JWT with "none" as its algorithm is a free ticket. Modify user and become admin, root,... Also, in poorly implemented JWT, sometimes user and password can be found in the payload.
To craft a jwt with "none" as the value for "alg", run:
The null signature attack
Second attack in this section is removing the signature from the token. This can be done by erasing the signature altogether and leaving the last period in place.
The blank password accepted in signature
Launching this attack is relatively simple. Just remove the password value from the payload and leave it in blank. Then, regenerate the jwt.
Also, with jwt_tool, run:
The algorithm switch (or key-confusion) attack
A more likely scenario than the provider accepting no algorithm is that they accept multiple algorithms. For example, if the provider uses RS256 but doesn’t limit the acceptable algorithm values, we could alter the algorithm to HS256. This is useful, as RS256 is an asymmetric encryption scheme, meaning we need both the provider’s private key and a public key in order to accurately hash the JWT signature. Meanwhile, HS256 is symmetric encryption, so only one key is used for both the signature and verification of the token. If you can discover the provider’s RS256 public key and then switch the algorithm from RS256 to HS256, there is a chance you may be able to leverage the RS256 public key as the HS256 key.
The jwt crack attack
JWT_Tool can still test 12 million passwords in under a minute. To perform a JWT Crack attack using JWT_Tool, use the following command:
You can generate this wordlist for the secret signature of the json web token by using crunch.
Once you crack the secret of the signature, we can create our own trusted tokens. 1. Grab another user email (in the crapi app, from the data exposure vulnerability when getting the forum (GET {{baseUrl}}/community/api/v2/community/posts/recent). 2. Generate a token with the secret.
Spoofing JWKS
Specify JWS URL with -ju, or set in jwtconf.ini to automate this attack.