Exploiting API Authorization
General index of the course
- Setting up the environment
- Api Reconnaissance.
- Endpoint Analysis.
- Scanning APIS.
- API Authorization Attacks.
- Exploiting API Authorization.
- Testing for Improper Assets Management.
- Mass Assignment.
- Server side Request Forgery.
- Injection Attacks.
- Evasion and Combining techniques.
- Setting up the labs + Writeups
BOLA - Broken Object Level Authorization
BOLA vulnerability allows UserA to request UserB's resources.
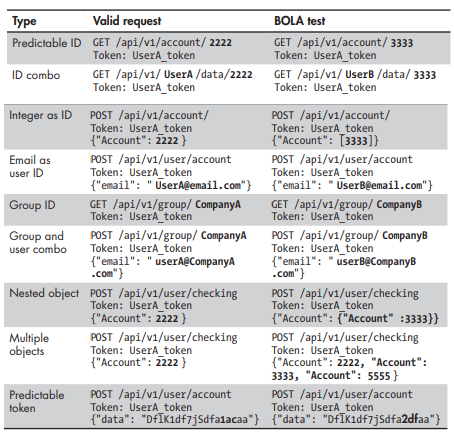
Methodology
- Create a UserA account.
- Use the API and discover requests that involve resource IDs as UserA.
- Document requests that include resource IDs and should require authorization.
- Create a UserB account.
- Obtaining a valid UserB token and attempt to access UserA's resources.
You could also do this by using UserB's resources with a UserA token.
BFLA - Broken Function Level Authorization
BFLA is about UserA requesting to create, update, post or delete object values that belong to UserB.
- BFLA request with lateral actions. UserA has the same role or privilege level than UserB.
- BFLA request with escalated actions. UserB has a privilege level and UserA is able to perform actions reserved for UserB.
Basically, BFLA attacks will consists on testing for various HTTP methods, seeking out actions of other users that you shouldn't be able to perform. Important: being careful with DELETE request.
Methodology
- Postman. Go through the collection and select requests for resources of UserA. Focus on resources for private information. Focus also on HTTP verbs such as PUT, DELETE, POST.
- Swap out your UserA token for UserB's.
- Send GET, PUT, POST, and DELETE requests for UserA's resources using Userb's token.
- Investigate code 200, 401, and responses with strange lengths.
BFLA pays special attention to requests that perform authorized actions.
Tools
- Postman: use the collection variables. Create specific collections for attacks.
- BurpSute: use the Match and Replace functionality (tab PROXY>OPTIONS) to perform a large-scale replacement of a variable like an authorization token.